What Are Vulnerability Scanner Tools and How Do They Work?
The advent of new technologies helps businesses to streamline their operations. Companies are leveraging next-gen technologies, and their functions are becoming more data-driven. However, as the dependency on data increases, enterprises are increasingly facing risks from hackers. They must have adequate processes in place to thwart data breaches. It leads to the increasing use of vulnerability scanner tools to find security gaps in the IT infrastructure proactively. Regular scanning of the IT framework can bring up the vulnerabilities which the attackers can manipulate.
What is a Vulnerability Scanner?
Businesses need to assess whether there are any vulnerabilities in their network. Relevant stakeholders must plug them, if there are any, to prevent any unwarranted data breaches. The phenomenon of vulnerability scanning involves automated scanning of the applications, networks, security apparatus, etc., proactively. The security team can undertake the scan in-house, or you can deploy expert consultants for this activity.
The vulnerability scanner tools will inspect the entire digital framework across the company and review it properly. There are various ways and means that hackers can exploit to gain access to the company’s data. The application will generate a report when the comprehensive vulnerability check is complete. The findings from the assessment can help the IT team to formulate robust strategies to improve their security status.
Erstwhile Challenges in Vulnerability Scanning
Traditional vulnerability scanners were monolithic systems present on the company’s servers and were required to alert the stakeholders of runtime threats. It was prevalent until businesses ran on-premises applications to support their operations. It was challenging to have the asset inventory updated, and it required a separate set of strategies and applications.
The advent of cloud technology requires critical changes in the working of these scanners. The cloud-based infrastructure is agile and scalable. The pipelines cannot handle security bottlenecks, and the scanning applications must match the pace of agile DevOps practices. The cloud architecture has a highly distributed architecture and can be serverless too.
The cloud native security workflows require holistic vulnerability scans while considering proper security best practices. The scanners must cover advanced devices like mobile devices, cloud components, IoT devices, employees’ devices, etc. The application must undertake continuous monitoring – a pivotal shift from the erstwhile periodic monitoring techniques.
Also Read: How to Stay Safe from SquirrelWaffle Malware
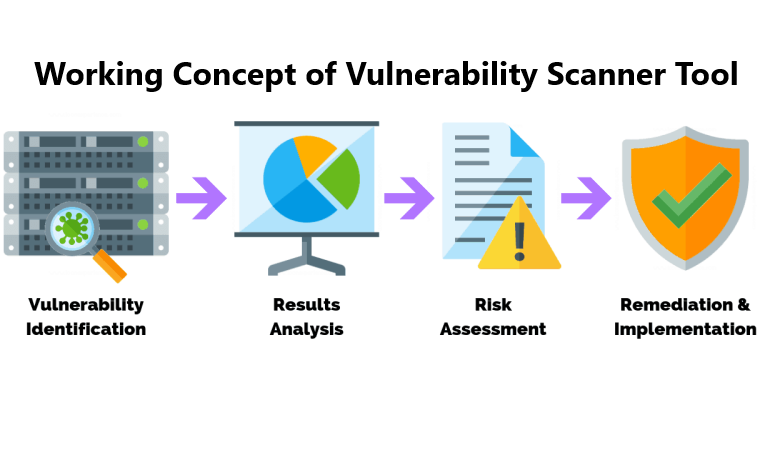
How do Vulnerability Scanner Tools Work?
The primary requirement of vulnerability scanner tools is to identify any possible vulnerabilities in the company’s framework. It can help your IT security team to focus on specific areas of interest. The vulnerability scan can detect and assess the possibility of an attack. You can determine any gaps in IT security and make suitable amends to thwart cyberattacks.
You can examine the threats, assess them properly, and prioritize them. When you find and rectify the threats, you can have policies to safeguard the IT framework from future threats. If there are any vulnerabilities, they can be classified based on internal policies, and you take the relevant actions. Some of the factors governing threat prioritization can be risk measurement, age, etc.
The final stage is having a detailed assessment report of the scan which can provide input on enhancing your cybersecurity framework. The focus is on continuous or periodic monitoring and letting the stakeholders take appropriate action. There are advanced automated solutions which can improve IT admin productivity.
Types of Vulnerability Scans
External and Internal Vulnerability Scans
External vulnerability scans cover the business components that are exposed to the internet and not restricted for internal use only. Businesses can run the scans from outside their network and aid in understanding the threats from the internet. It also scans the applications and servers accessed by the traffic between the internet and the firewall.
Internal vulnerability scans involve scanning the components which intruders can access once the threat has access to the local network. It assesses the flaws which the hackers can exploit by moving across the different systems inside the company’s network. It assesses how the network is segmented and configured. After identifying the vulnerabilities within the network, take steps to prevent the damage. The application and system security are tightened and not exposed to hackers.
Initiate vulnerability scans by mapping the business’ inventory. Set the priorities for the asset inventory based on the sensitiveness of the data they store. Few industry standards require companies to undertake both external and internal vulnerability scans. You must undertake these scans on changing the firewall settings or after adding new network components. Usually, you can undertake them once every quarter or according to your IT policy.
Authenticated and Unauthenticated Scans
There are scanners with proper credentials and can access precise system data like software configurations and versions, operating system versions, etc. They use login credentials to collect accurate information about the applications available on the scanned devices. They collect more data and can discover more vulnerabilities than an unauthenticated scan. These scans require user accounts to dig into your network and deeply assess various aspects of the network. It can evaluate password sensitivity, threats around installed applications, etc.
Unauthenticated scans can be performed remotely without sophisticated knowledge. It allows scanners without proper credentials to assess the services available over the network. It can send packets to find open file shares, operating system versions, statuses, etc. Once these details are available, it will check the database and assess the possible vulnerabilities in those systems. It can help you assess which components a hacker can access in your network without acquiring your user credentials.
Limited and Comprehensive Vulnerability Scans
A comprehensive vulnerability scan can explore and identify vulnerabilities across all the devices on the network. It can include laptops, smartphones, servers, firewalls, switches, etc. It can also scan all installed software, operating systems, user information, etc., covering all the devices on the network. While it can utilise a lot of bandwidth, there is no risk overlooked. You receive a comprehensive report that can be used in future strategies to prevent network attacks.
A limited scan will focus on particular devices or software. It will target specific risks and protect them comprehensively against future threats.
Web Application Vulnerability Scanners
These vulnerability scanner tools can help assess vulnerabilities in websites or other web-based software. It focuses on the application’s code and can search for common flaws like command injections, XSS, SQL injection, etc. It is a critical component of application security testing and can work against standard web app hijacking techniques.
Security teams can use these tools with SAST tools (static application security testing) to undertake automated scans of uncompiled code for vulnerabilities. The DAST tools (dynamic application security tools) can scan compiled code automatically across different environments. You can integrate vulnerability tests into DevOps and QA procedures.
When you plan to secure web applications or websites, a periodic scan may be detrimental to overall enterprise-level security. There can be incidents which can lead to issues in vulnerability scans. It becomes necessary to undertake continuous scans to monitor the network and deploy automated policies to ensure the application upgrades are on time.
HCL can help Ensure Enterprise-Level Security
HCL Appscan is one of the application security scanning tools to protect your business from attacks. It can pinpoint vulnerabilities and help in fast remediation across any stage of the software SDLC. It uses IAST (Interactive application security testing) technologies. There is an agent present on the web server of the tested application. It can monitor the traffic during runtime and assess for any security gaps.
IAST, unlike DAST, can monitor the system tests and the traffic sent during SAST or DAST scans. It reports to the Appscan Enterprise on the security issues found in the application. The developers can write code with fewer security problems and allows teams to collaborate on the scanning processes. Web application vulnerability scanners like Appscan Enterprise are ideal for your business as it supports IAST, DAST, and SAST features. You can choose Appscan on Cloud for applications available on a cloud infrastructure.
Conclusion
Businesses face the risk of cyberattacks constantly. A successful attack can ruin the brand equity and lead to several legal repercussions. You must be cautious about any security gaps, find them proactively, and fix them. Popular application scanners, like HCL Appscan, can support several code languages and make scanning files easier. It is ideal for developers who prefer a friendly platform.




